Product & Service Introduction:
OpenText SMAX is comprehensive service management software that delivers efficient IT Service Management (ITSM), IT Asset Management (ITAM), and Enterprise Service Management (ESM). Powered by embedded analytics and machine learning, it is easy to use, easy to extend, and easy to run anywhere.
Technical Description:
Security vulnerability has been identified within the ITSM component of OpenText SMAX. This vulnerability, due to an authorization flaw, allows authenticated users to submit requests under the names of others. Given that the system syncs with Active Directory, assigning unique IDs to users, exploitation of this flaw can enable unauthorized request modifications or manipulations on behalf of unsuspecting users.
Steps to Reproduce:
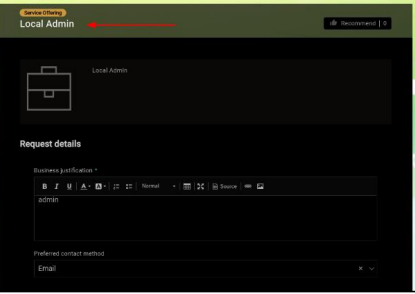
Start the Submission Process: Log into the ITSM System using an Active Directory account and select a request type. In this example, we’ll use “local admin account.”
Prepare Request: Click on the request interface to input any title and justification for the request.
Intercept and Modify: Using a proxy tool, such as “burp suite,” intercept the request being sent.
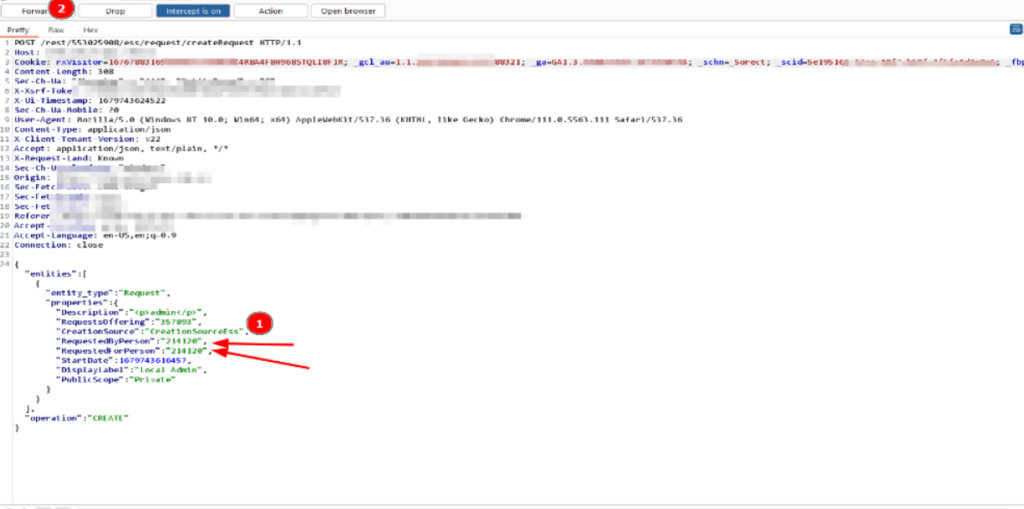
Impersonate a Target: Within the intercepted request, change the User ID to your intended target’s ID and then forward the request.
Post submission, the victim won’t receive any email notification, thereby remaining unaware of this unauthorized activity.
How to a user Identifier?
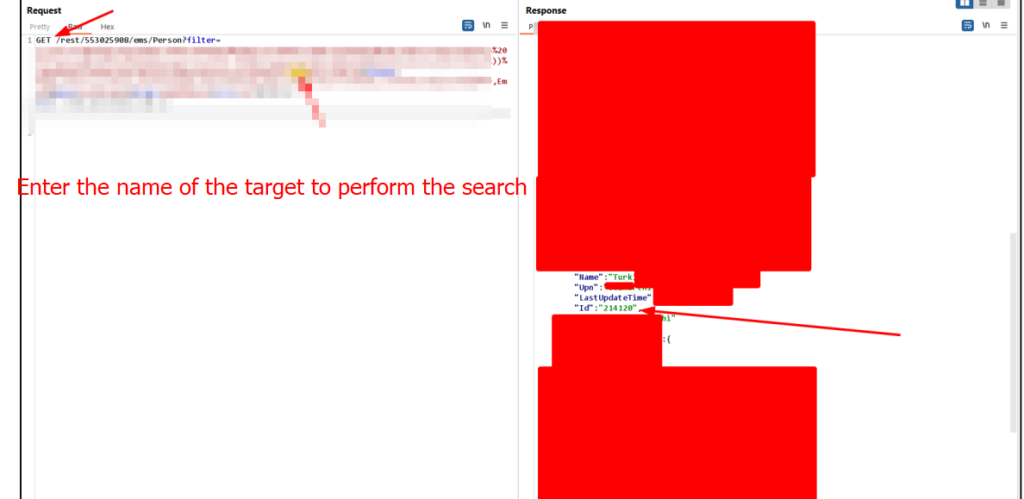
Solution – Fix & Patch:
Micro Focus has made the following mitigation information available to resolve the vulnerability for the impacted versions of SMAX/AMX/HCMX:
- SMAX 2023.05.P1
https://docs.microfocus.com/doc/SMAX/2023.05/202305P1
- AMX 2023.05.P1
https://docs.microfocus.com/doc/AMX/2023.05/202305P1
- HCMX 2023.05.P1
